
How confident are you that the security models and measures in your organization are doing their job as well as you think they are? Or, better still, have you ever considered that the information security you have in place is acting more of a barrier to your development teams than malicious intruders? It is possible that the one thing your security is excelling at is preventing your teams from practicing Agile.
When talking about security, by default, most assume that bigger is better. After a breach occurs, the response is usually to upgrade, spend more money, and invest in newer technologies. However, I’d argue (and will) that you don’t need to invest millions of dollars to keep your organization safe. Don’t believe me? Take a look at the below diagram that demonstrates how not only a company with best in class security but an actual security company, was still experiencing spam, phishing, and malware in over 9% of their emails.
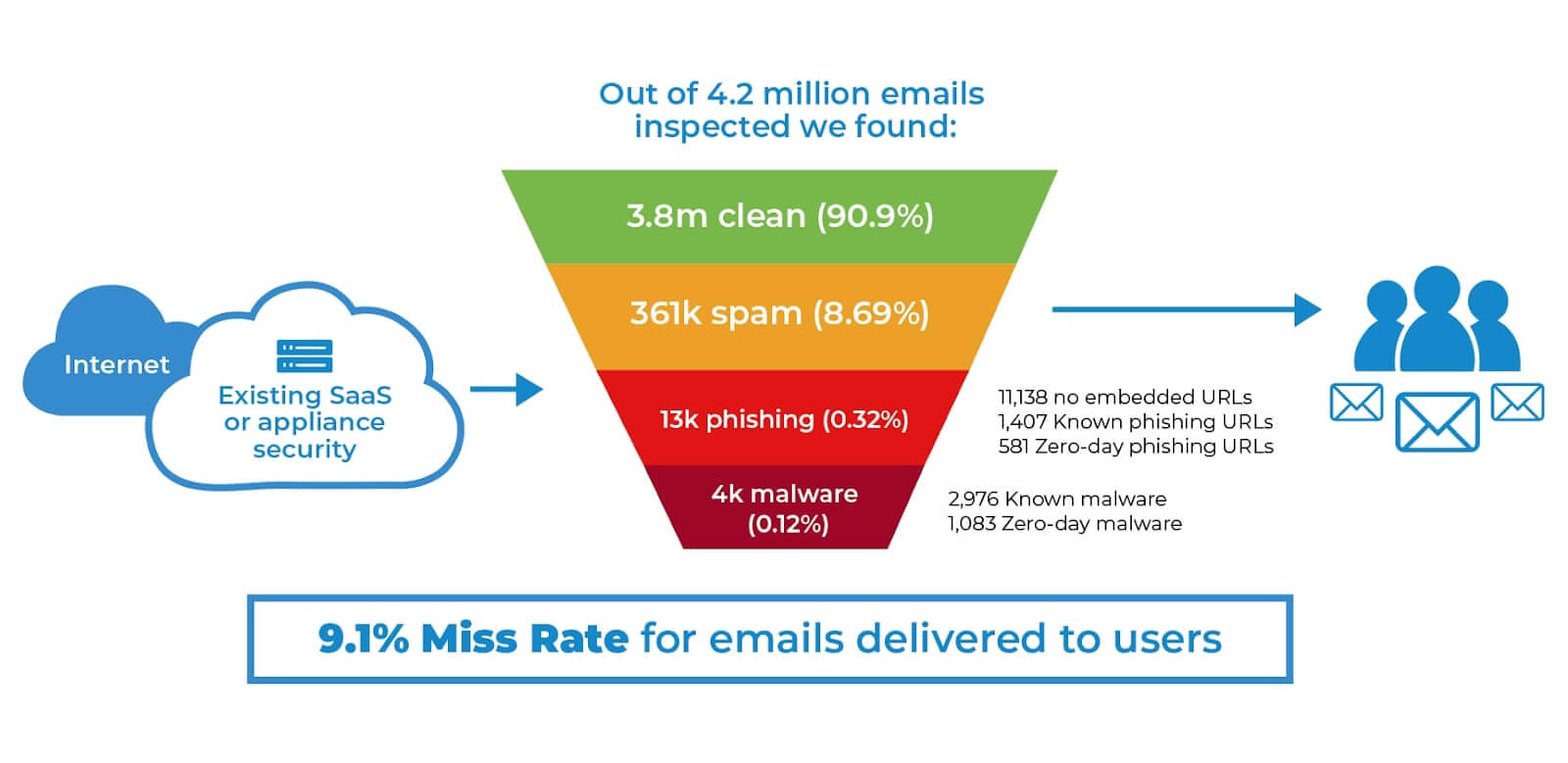
So what’s the solution? I propose that security problems be treated like any other problem, and most problems can’t be solved by throwing money at them. They can, however, be solved with some intelligence. Today, I will show you our intelligent approach to enterprise-grade security that is designed not only for protection but also for agility.
A New Stance on Information Security
In a world where everything is connected, cybersecurity must become more comprehensive, adaptive, and collaborative. As complexity grows, companies should create approaches to address threats across the different layers; application and service, software and hardware interfaces, physical network architecture, and edge devices.
This will require some companies to take a new stance on security, an adaptive, thorough, and collaborative approach. That’s because security exists in a business context, not only a technical one. Technical experts cannot efficiently solve the problem without understanding the underlying business complications.
With every organization at risk, preparation is the key. Here are the first steps:
1. Prioritize Assets and Risk by Criticality
No matter your size or industry, all companies are exposed to some degree of threat, attack, or malintent. However, given the wide variety of industries and verticals that exist, it stands to reason that generic security solutions won’t suffice. Rather, it is critical to tailor security and control towards the specific industry you’re in and the current threat levels that exist within it.
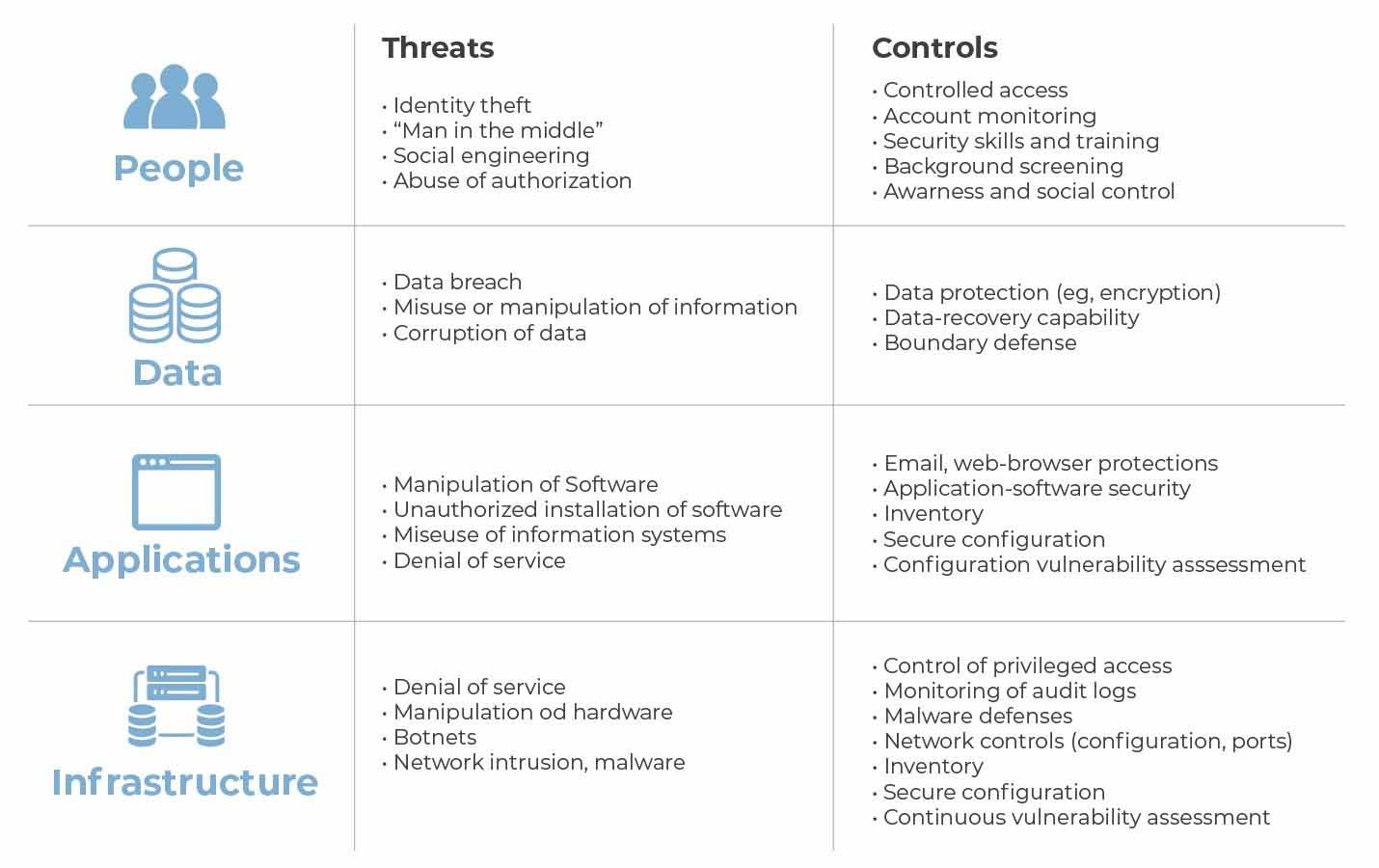
People have Threats of Identity theft , Man in the middle, Social engineering, Abuse of authorization and controls on Controlled access, Account monitoring, Security skills and training, Background screening, Awarness and social control. Data has Threats of Data breach, Misuse or manipulation of information, Corruption of data and controls on Data protection (eg, encryption), Data-recovery capability, Boundary defense. Applications have Threats of Manipulation of Software, Unauthorized installation of software, Miseuse of information systems, Denial of service and controls on Email, web-browser protections, Application-software security, Inventory, Secure configuration, Configuration vulnerability assessment. Infrastructure has Threats of Denial of service, Manipulation od hardware, Botnets, Network intrusion, malware and controls on Control of privileged access, Monitoring of audit logs, Malware defenses, Network controls (configuration, ports), Inventory, Secure configuration, Continuous vulnerability assessment.
2. Establish Effective Controls and Processes
Every organization should consider establishing the right controls to physical and logical assets. Once assets are identified, define them critically so that proper control can be applied accordingly.
Traditional approaches on how controls are implemented and access are granted to assets are not particularly suited for today’s digital world. Companies need to implement GUI and API based access /provisioning while embracing new technology like Artificial intelligence, Automation, and Big Data to cope with the ever-increasing threats, building controls around them.
3. Consolidate Organizational Threats and Implement Universal Governance Model
The way most organizations’ security is structured is outdated and inefficient. Physical security, information security, business continuity, and crisis management are often their own entities. In truth, they should be consolidated and aligned to serve the organization better. The goal is to achieve “Security by Design,” and that starts with a firm foundation and architecture for data, system, and security.
Information Security Transformation
Most of the organization, in some way or form, is in the process of digital transformation. It is vital to undergo information security transformation to keep up with new threats. Although the security team’s purpose is safety and protection, I often witness a misalignment between the security team and development teams that delays new features or missed business opportunities. The goal of nearly all organizations is speed and agility, and digitizing your security not only helps you achieve that but will also enhance your security itself.
However, before that happens, an organization’s security needs to transform to improve decisioning, bring value to the business, and enable new technologies and methodologies like cloud, Agile, and DevOps.
1. Decision Making through Quantitative Risk Analysis
Security is essentially deciding which risks to accept and how to mitigate them. Sadly, making those decisions isn’t easy, but that changes when you use quantitative risk analysis. This type of analysis breaks down information and segments it. It provides behavioural analysis to identify signs of internal threats, along with risk-based authentication, which considers metadata – user location, recent access logs, etc. All of these can fit into a comprehensive dashboard that ties business assets, threats, vulnerabilities, and potential mitigation plans together to help organizations make the right decision.
2. Security and the Value Chain
No matter their size, practically every company, in some shape or form, exchanges sensitive data across networks about their customers, suppliers, or partners. Rather than view this as a problem, take it as an opportunity to build security into your business’s value chain. This step becomes even more critical when you consider the rise of digital transformation and IoT.
Product companies should consider security as a core feature when designing products. Service companies should use threat intelligence reports to access supplier/partner technology externally and assess the risk of compromise, allowing security data to be used and leveraged in negotiations.
3. DevSecOps and Agile Methodology
IT operations in business are transforming to be more dynamic and agile. And on par with this transformation needs to be an agile security model to enable new technology and methodologies.
Here are a few steps I would recommend to ensure your information security and keep up with technology:
- Security access needs to be moved from ticket to API based. This means all interaction/integration should be automated as part of the software development lifecycle. This allows developers to access real-time to IAM service, vulnerability scans, and applications through APIs without the need to raise a ticket and wait for it.
- Organize the security team into scrum or kanban teams.
- Transform Team lead or Sr.Dev as the security champions who act as Product Owners (POs) for security best practices in Agile teams, similarly to POs for a product roadmap.
- Enable cloud-native security model, allowing developers to gain access to instantaneously.
- Work with architecture and infrastructure teams to bring security service into standard solutions and create large sets of data for analysis.
Take away
While security and the need for it will only continue to grow alongside our digital evolution, it seems as though it will never be at par. Despite how much organizations spend and no matter what latest and greatest technology they have implemented, it seems it will only be a matter of time until the malicious occurs. Perhaps, that is because the historic security approach is flawed.
As I mentioned earlier, and as I am sure you have all heard before, it isn’t often you can solve a problem by throwing money at it, and security is no exception. Instead, I propose we turn to an intelligent approach, one that, as I have outlined, not only keeps your organization safe but complements and brings value to the business.
It is possible. You just need to give a little bit of forethought to your approach.



